Home > Monitoring > Phishia CTI
Phishia CTI
Anticipate threats, protect your strategic assets
Phishia CTI: from detection to the neutralizationWe provide you with continuous threat intelligence to protect your critical systems and guide your cybersecurity decisions.
PhishiaCTI cluster in figures
Cyber threat intelligence, what is it?
Cyber threat intelligence (CTI) is intelligence about the threats you face.
We monitor and analyze what's relevant to you, then take the right action to avoid an incident or limit its impact.
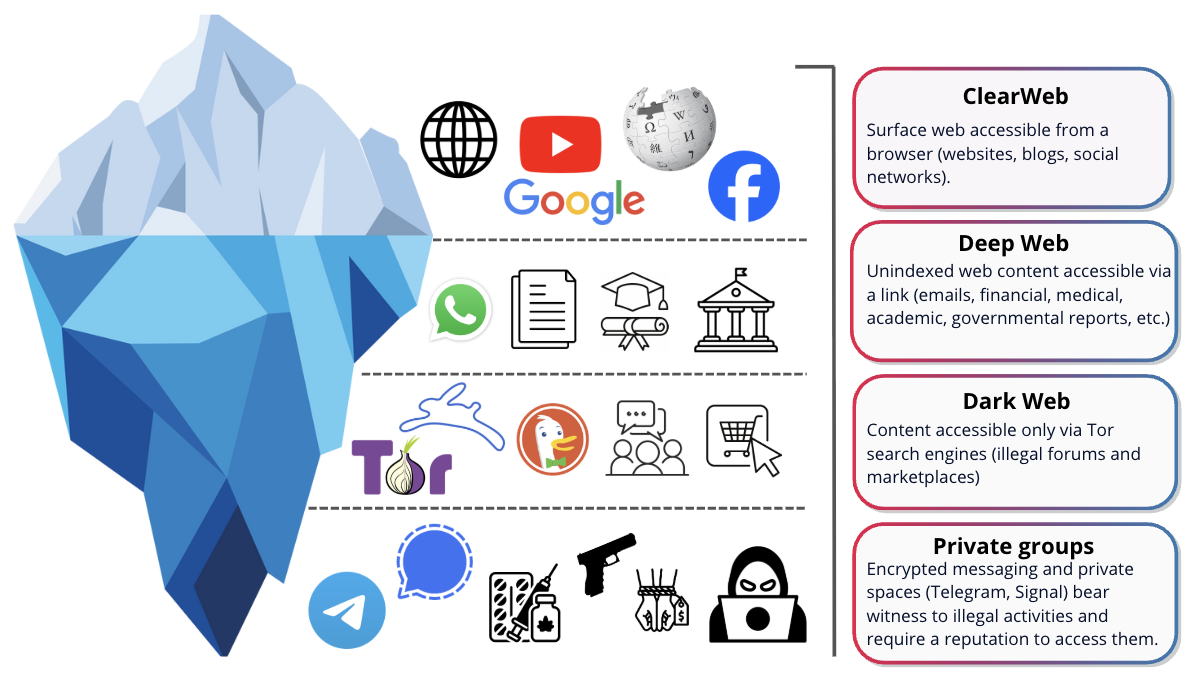
Flare X Phishia, a winning combination
Flare, Phishia, our web/deep/dark sensor, detects and retrieves via targeted searches (name/company, BIN, email, phone, domain/URL, IP, login, password...), and contributes to the management of your external attack surface (EASM). Phishia qualifies, prioritizes and implements the response (resets, blocking, SIEM/EDR rules).
We therefore classify each leak encountered according to an indicator developed in-house, ranking them by priority for action:
Criticality 1
Minor
Criticality 2
Significant
Criticality 3
Major
Criticality 4
Review
CTI: anticipating attacks
Before each attack, signals appear
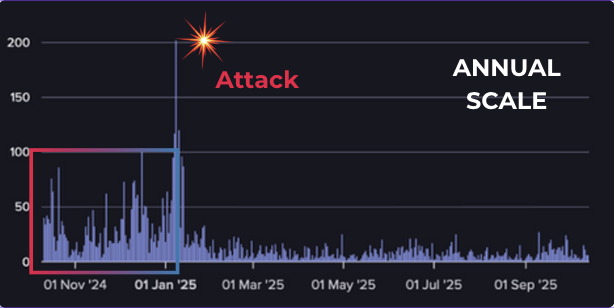
On the Dark Web, malicious actors trade, recruit, test tools or seek to monetize access.
This creates unusual business-related activity.
We detect and correlate these signals to trigger preventive measures, to anticipate and thwart attacks.
For example, in the attached red box :
By analyzing how often a company appears on the Dark Web, our tools identify any unusual rise in activity, indicative of a potential attack.
In the end, there was no shortage of them. After the rise from November to January, an attack did take place. With this type of surveillance, the attack would have been avoided.
Our recommendations
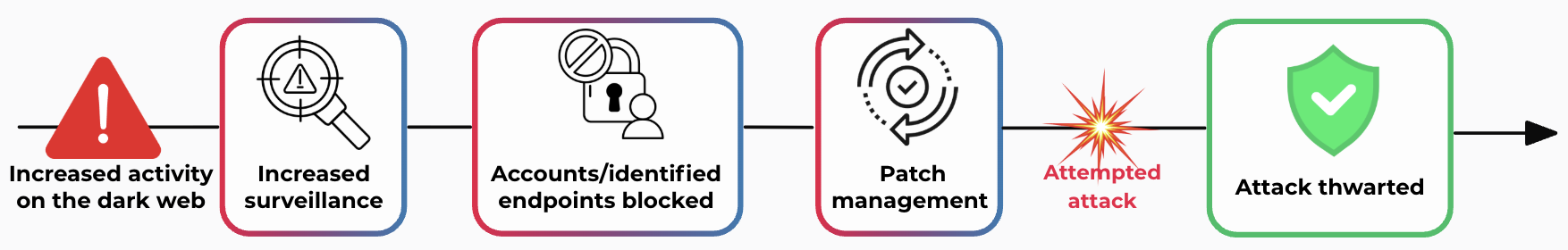
Incident follow-up process
We continuously monitor the DW for any suspicious activity: access sales, data leaks, malware, VPNs, attack preparations, exchanges between players...

Targeted survey of the service or asset in question to assess actual exposure and concrete risk, in order to distinguish between proven threat and false-positive/noise.

Within the authorized framework, we verify the reality and scope of the threat by means of appropriate checks (e.g. testing the validity of a password).

Depending on the criticality established by our experts, we alert you immediately with a clear playbook, accompanied by a concise report containing all incident-related information.

Phishia CTI offer
Included in the offer
- Analysis of all data leaks and remediation plan
- Testing the validity of credentials
- Prioritizing the criticality of credentials
- Live alternating for the most critical alerts
- Monitoring compromised end-points
- Detailed bi-monthly reporting
From
30/month
per ID
* unique identifier that we monitor for you (domain name, IP, personal e-mail...)
Phishia CTI Flash
Visit 15 days maximum, Our Flash CTI offer gives you a clear overview of your exposure on the dark web.
For each leak identified, you receive a remediation plan and detailed concrete recommendations to sustainably reduce your display surface and prevent it from happening again.
1.
Setting the scene
Definition of critical domain names, VIPs and portals to be monitored.
2.
ID-MDP pair testing
3.
VIP advanced search
4.
Remediation & security plan
5.
Final report
Phishia CTI Flash offer
Included in the offer
- Tests of all credentials sent by Flare
- Plan to reinforce platform safety
- Leak detection for X VIP
- Support for remediation of identified leaks
- Detailed report
What we need
Domain names
VIP list
Connection portals
Our blog
Discover the latest news and trends in SOC & CTI.



