Forget the image of the hoodie-wearing hacker typing neon-green lines of code all night long to «brute-forcing» your servers. In 2025, the reality is much more mundane, and frightening: your network access may already have been sold this morning, for the price of a BigMac menu.
Welcome to the age of Stealer Logs, the silent threat that renders your password policies obsolete.
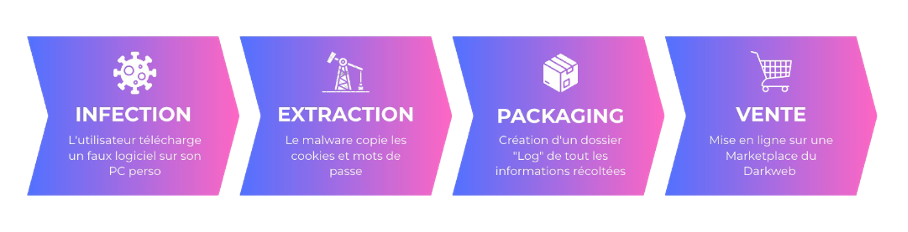
The mechanism: How your digital identity is "zipped"
Infostealers« (as in Lumma, RedLine or Vidar) are discreet malware. They don't need to break into your systems. They are often installed via cracked software downloaded by a telecommuting employee, or a harmless attachment on a personal e-mail.
Once active on the machine, the malware doesn't just steal passwords. It steals everything:
- Visit identifiers saved in the browser.
- Information from credit cards.
- Browsing history.
- And above all: Session Cookies.
Therein lies the critical danger.
Why the MFA won't always save you
It's a cold shower for many CIOs. We often think that Multi-Factor Authentication (MFA) is the ultimate rampart.
But if an attacker steals your Session cookie valid via a Stealer Log, it doesn't need your password or SMS code. It imports this cookie into its own browser, and the target site (your CRM, your Office 365 access, your VPN) thinks it's you. It is already connected.
The crime supermarket
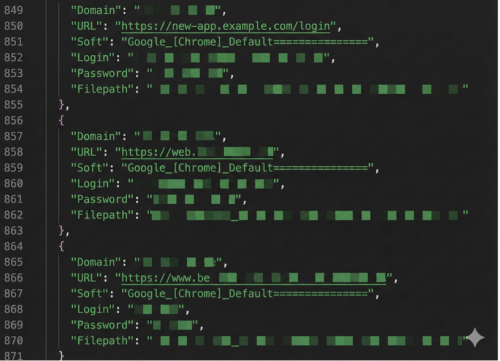
This stolen data does not remain on the hacker's computer. They are massively aggregated on automated marketplaces (such as Russian Market or private Telegram channels).
The business model is industrial. A «Log» (the complete file of a victim or a group of computers) generally sells for around 10$. For this price, the buyer gets access to all accounts : Netflix, Facebook, as well as VPN access for their company.
This is how the majority of today's Ransomware attacks begin: with a simple purchase from 10$ weeks before the final attack.
Regain control with CTI
Digital hygiene is essential, but it relies on human beings, who are fallible. You can't prevent an employee from mistakenly installing malware on his or her personal PC, but you can find out if his or her professional credentials have been leaked.
Visit Cyber Threat Intelligence (CTI) is not just about looking at your internal logs, but also at the outside world.
At Phishia, We continuously scan these underground markets. We're able to spot whether identifiers belonging to your @your-company.com domain are currently for sale in logs, even if the infection took place on an employee's personal computer.
Immediate action: the CTI Flash audit
Don't remain in doubt. To know is to be able to anticipate.
For the launch of our CTI offer, Phishia proposes a pragmatic approach: CTI Flash offer. This is a «one-shot» audit to take immediate stock of your exposure.



