We often hear about dark web as a mysterious place reserved for pirates. In reality, it's a where stolen sensitive information is sold or displayed, sometimes for months without the organizations even knowing it.
The web iceberg: surface, depth and dark zones
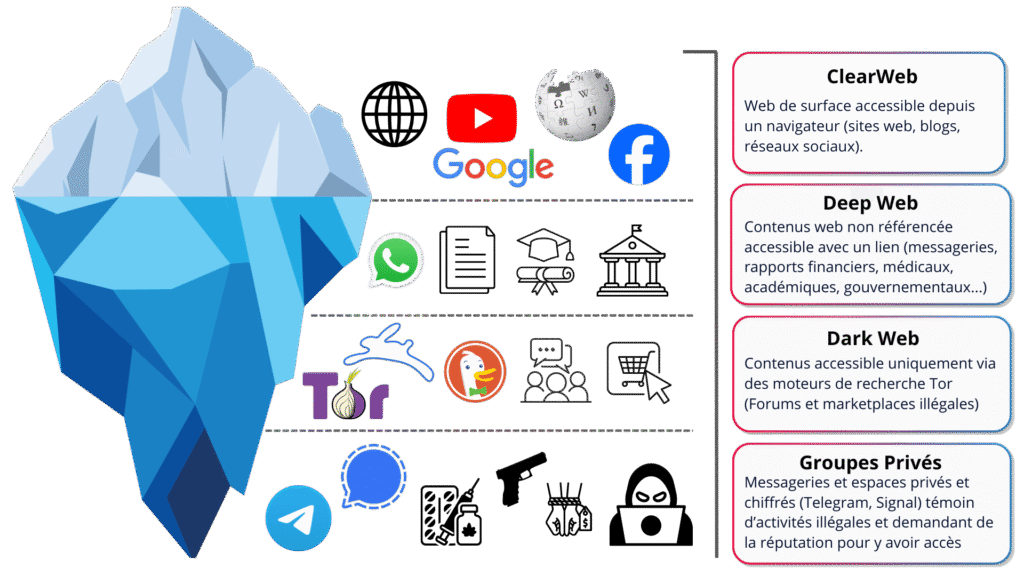
Clear Web - the visible part
The “above the surface” layer: public websites, media, blogs, social networks, all just a few clicks away via Google or other search engines.
Deep Web - hidden but legitimate
Beneath the surface: private spaces (messaging systems, extranets, internal portals), documents and reports accessible only by link or account. Not indexed, but perfectly legal.
Dark Web - the danger zone
Access via specific tools like Tor, with closed forums, marketplaces and private groups often used for reselling data, attack tools or compromised access.
It is precisely on these deeper layers that the Cyber Threat Intelligence (CTI) will look for weak signals and leaks.
What sensitive information is sold or exposed on the dark web?
On the dark web, attackers don't sell “files” in the abstract. Above all, they sell access and elements of confidence to build an attack.
Here are a few concrete examples from the cases we encounter at Phishia:
Login credentials
These are the couples login / password for :
- internal portals (intranets, agent portals, donor spaces, etc.),
- business services (CRM, HR tools, payment and donation solutions),
- mailboxes or administrator accounts.
These identifiers can come from :
- from a compromised workstation (malware, phishing),
- reuse of a password already stolen elsewhere,
- negligent service provider.
In our analyses, we regularly see lists of hundreds of credentials associated with a single domain name, with very different levels of criticality depending on the account concerned: from “non-sensitive” access to accounts that can modify financial data or access confidential information.
Personal and financial data
For associations and public bodies alike, we find, for example :
- donor data (contact details, donation history, sometimes SEPA mandate),
- user or beneficiary data,
- information used to impersonate a person or organization.
Possible consequences: fraud, misappropriation of donations, loss of trust, regulatory sanctions.
Technical access and infrastructure elements
On dark web forums and marketplaces, you can also find :
- access to Internal VPNs,
- RDP sessions (remote control of a server or workstation),
- information on unpatched vulnerabilities,
- sale of malware targeting a specific type of organization or technology.
These elements are used to prepare a larger attack (e.g. ransomware).
Raw“ leaks to be sorted
The leak lists are not always neat and tidy. They include:
- real identifiers that are still valid,
- obsolete identifiers,
- duplicates,
- false positives.
One of the key roles of a CTI cell is precisely to sort and qualify to distinguish the real threat from the background noise.
Why is this problematic for an organization?
This information is used to :
- d’enter your systems without triggering an alarm,
- to prepare a targeted scam (phishing, president fraud, donation scams),
- from resell your data to other criminal groups,
- tarnish your image if the leak becomes public.
Worst-case scenario: your login details and data have been circulating for months or even years on specialist forums, and you don't know.
How Phishia's CTI offer can help you
Visit Cyber Threat Intelligence (CTI) is to proactively monitor everything that's happening around your organization on the surface web, the deep web, the dark web and within certain private cybercriminal groups.
At Phishia, we rely on Flare, our web/deep/dark sensor, which automatically tracks leaks linked to your credentials (domain names, e-mail addresses, IP addresses, logins, passwords, etc.), and on our analysis expertise to qualify, prioritize and treat each leak.
In concrete terms, our CTI approach combines several building blocks: a continuous monitoring useful sources (access sales, data leaks, compromised accounts, malware), from targeted audits to test the validity of certain identifiers within the legal framework, a OSINT contextualization to understand which services are affected and what impact this may have, then a criticality assessment with immediate warning in the event of a serious leak and a remediation plan(password reset, access blocking, configuration hardening, new SIEM/EDR rules, etc.). All consolidated in a regular reporting Detailed reports, activity indicators and monitoring of threat trends aimed at you.
The objective is simple: alert you as soon as possible when your information appears on the dark web or in high-risk areas, and help you correct the situation before it becomes a major incident.
Want to know more? Visit our CTI offer :


