When a large public organization (city, hospital, metropolis...) suffers a massive cyberattack, the dominant impression is often :
“They fell on us all at once, we couldn't see it coming.”
Except in reality, a major attack almost never begins on Monday at 9 a.m..
Weeks - sometimes months - before the final attack, activity around the organization increases sharply on the dark web :
- stolen identifiers,
- VPN access for sale,
- private discussions between cybercriminals,
- access tests on various portals.
With a genuine Cyber Threat Intelligence (CTI), these signals can be seen, analyzed... and transformed into defense actions before things get out of hand.
Before the attack: when the dark web gets restless
Take the typical case of a large community or organization hit by ransomware:
Months before: first discreet leaks
In leaked lists or on certain forums :
- from internal e-mail addresses associated with passwords,
- accounts linked to business portals,
- technical access (VPN, RDP, etc.) sold at low prices.
At this stage, the organization is not yet a “priority target”, but it is on the attackers' radar:
it has interesting data, and doors begin to open.
A few weeks before: net increase in activity
Gradually, activity related to the organization's domain name or addresses increases sharply :
- more mentions in leakage databases,
- more identifiers tested or offered for sale,
- targeted discussions around its services (such as agent portals, administrative accounts, etc.).
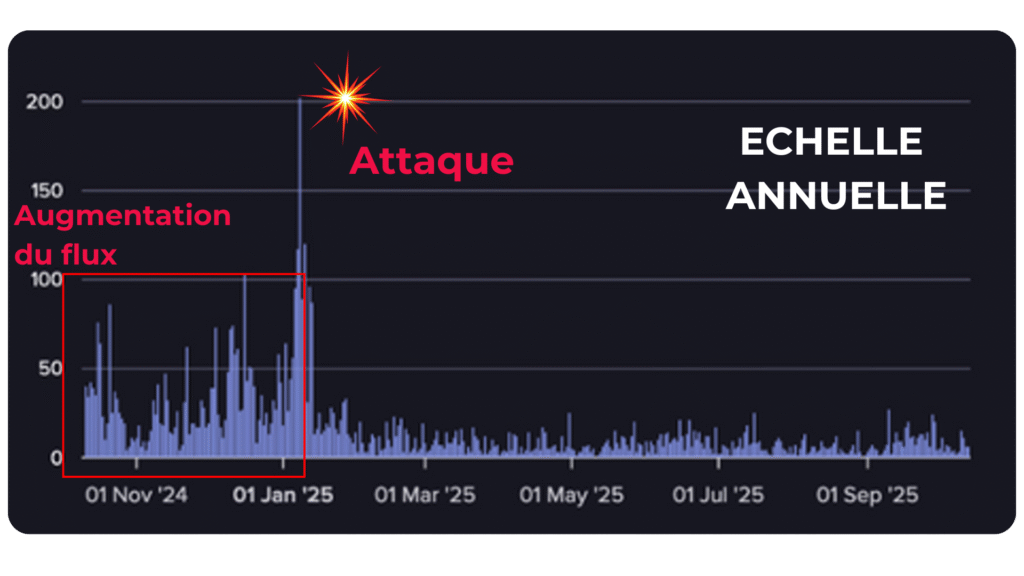
You can clearly see a jump from the usual “base line.
For a CTI eye, it's a red flag:
“Someone is much more interested in this organization than usual.”
Just before the attack: ready-to-use access
In the days leading up to the attack:
- certain accesses are tested (connection to portals, verification of identifiers),
- access brokers“ resell reliable entrance doors,
- ransomware groups are beginning to position themselves.
When the attack finally begins, preparation work is long over.
Encrypting systems is only the last step.
What well-structured CTI monitoring would have seen
With real CTI capability in place, this scenario no longer looks like a complete surprise.
In concrete terms, CTI will :
Continuously monitor useful sources These include the «classic» web, the deep web (private spaces, encrypted channels), the dark web (closed forums, marketplaces, private groups) and public or semi-private data leakage databases.
Objective: report anything that concerns your organization
(domain names, e-mail addresses, trademarks, known IPs, main portals, etc.).
Qualify what comes up : it's not a matter of saying “we've found some stuff”, it's a matter of distinguishing what's really serious: an expired generic identifier remains of limited impact, whereas a valid VPN account with extended rights or an admin account on a critical internal portal reaches maximum criticality.
For each event, a criticality is assigned according to the sensitivity of the access, its functional scope and its potential for exploitation by an attacker.
Highlighting trends : is precisely what CTI Rather than treating each leak as an isolated case, it tracks the volume of leaks linked to your organization, pinpoints unusual peaks in activity and detects repeated discussions around your access or systems.
This is where the famous “before/after” comes into play: a relatively stable, normal noise level, followed by a period of abnormal agitation before the attack, which signals an escalation of risk and allows us to anticipate rather than suffer.
Phishia's concrete contribution to the CTI process
In the Phishia, We don't just “watch the dark web”. We apply a structured approach to see attacks coming and help react in time, before the incident turned into a major crisis.
In the case of an attack that paralyzes a large community or hospital, a CTI really up and running would have enabled :
Early warning : as soon as the first really noticeable leaks (critical accounts, valid VPN access, admin credentials...), when activity around the organization goes beyond normal levels.
Take targeted measures password reset, token invalidation, enhanced authentication (MFA, geographic restrictions, IP filtering), verification of exposed portals, quick access audit in leaks.
From “reactive” to “preventive” These include cutting off or closely monitoring compromised access, and controlling the most sensitive accounts, prepare the IT department, CISO and management to increased risk rather than discovering the leak after server encryption.
We can't promise that any attack would have been prevented at 100 %, but a well-exploited CTI greatly reducesthe probability of success, limits the extent of the damage... and avoid the general surprise effect.


