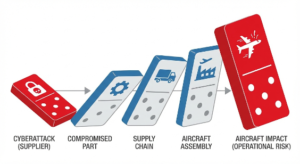
Aeronautics is a model of reliability, security and traceability. Yet it has become a prime target for cybercriminals, not by striking at the major airlines or manufacturers, but by targeting the link reputed to be the weakest: supply chain.
It's no longer your safety that's at stake, but that of the entire system, as required by the new European directives.
The new risk perimeter: From internal to ecosystem
An attack by Supply Chain occurs when a hacker exploits the vulnerability of a supplier, often smaller and less secure, to reach the final customer (aircraft manufacturer or operator).
Why is the Aero sector so vulnerable to this domino effect?
- Privileged trust : Suppliers have privileged access to customer information systems (drawing exchange platforms, maintenance software, critical parts databases).
- Regulations : The new requirements of the European Aviation Safety Agency (EASA), notably the IS share, require operators to ensure the safety of their products. ecosystem. A supplier's negligence can now result in sanctions and suspension of operations for the end customer.
This is a legal obligation of vigilance that extends to all players in the chain.
The threat of Lateral Intrusion
The risk is no longer limited to data theft (as was the case with the Stealer Logs). In the supply chain, it's a lateral intrusion :
- Compromise: A subcontractor (e.g. a fleet management software publisher) is hacked via a forgotten access or a simple vulnerability.
- Propagation : The hacker then uses the subcontractor's legitimate access to inject malicious code or exfiltrate critical data from all its customers simultaneously.
- Consequence: Stopping production lines, modifying technical documentation, or paralyzing a navigation system.
CTI at the service of aeronautical resilience
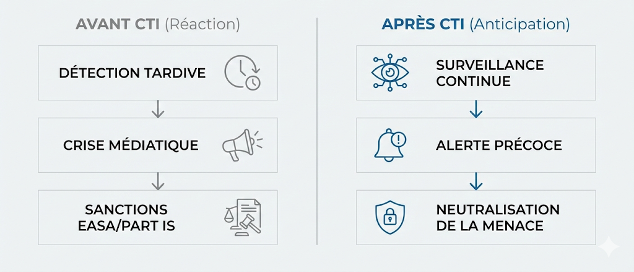
Faced with this systemic threat and the imperatives of compliance (Part IS), Cyber Threat Intelligence is becoming an indispensable audit and resilience tool.
Visit CTI Phishia allows you to adopt a strategy of extended surveillance :
- Third-party monitoring : We're not just looking to see if your identifiers are on the Dark Web, but also those of your strategic suppliers mentioned in your documentation.
- Early detection : Locate groups of pirates (e.g. Initial Access Brokers IAB) which target IT systems in aeronautics and industry.
- Proactive Compliance : Provide the proof of vigilance needed to meet the increased regulatory requirements of EASA and Part IS.
Partnership beyond the perimeter
For players in the aeronautics industry, CTI is not a cost, but an investment in the future. operational continuity and the regulatory compliance. Phishia gives you the visibility you need to identify and neutralize these risks before they paralyze an entire industry.
Whether you're a major client concerned with compliance IS share, or a critical supplier who must guarantee the highest level of safety, our CTI Classic offer is your ongoing assurance of the integrity of your ecosystem.


